Google released an update for Google Chrome Stable Stable on March 25, 2022. The emergency update patches a 0-day security issue in the web browser that is exploited in the wild according to Google.
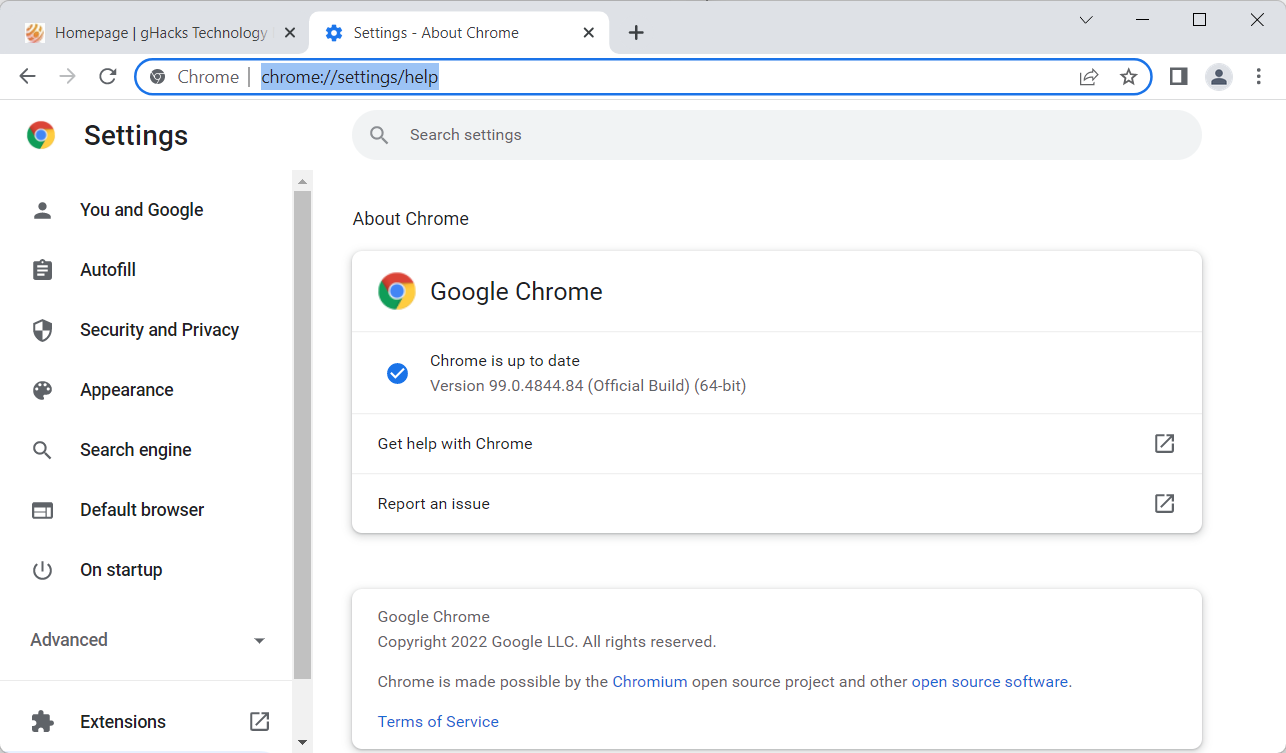
The update brings the Stable version of the browser to version 99.0.4844.84.
The update is already available for all supported desktop systems and Google notes that it will roll out automatically to all devices “over the coming days/weeks”. Chrome users may want to speed up the installation of the security fixes in the following way:
Google Chrome displays the version that is installed on the page that opens. An update check is run and any update that is found will be downloaded and installed. Chrome should pick up the released security update.
The release announcement posts for the Stable version, on the official Google Chrome Releases blog provides some information on the patched vulnerability.
The update fixes a single security issue that is rated as high. High is the second highest classification after critical.
[$TBD][1309225] High CVE-2022-1096: Type Confusion in V8. Reported by anonymous on 2022-03-23
Google notes that it is aware that an exploit exists for the vulnerability and that it is already used in attacks. The company does not provide additional information on the issue at this point. How the attacks are performed and their scope is unclear at this point.
The fixed security issues is the second 0-Day vulnerability that Google patched in 2022 in the Chrome web browser. The first security update was released in February 2022 to address an issue that was exploited actively at the time as well.
Chrome users should install the security patch as early as possible to protect the browser and their data against attacks targeting the issue. Google released an update for the Extended Stable channel of the browser as well on the same day, but makes no mention of a patched security issue in the announcement.
Now You: how often and when do you update your browsers?
lets face it, chromium is insecure – patching zero-days used in the wild is becoming a weekly occurrence
@osaka jimi
> chromium is insecure
Not more so than any other browser.
It has 80%+ market share, thus is the most attacked.
Firefox is a complete joke: https://madaidans-insecurities.github.io/firefox-chromium.html (article has recently been updated as well)
Many years ago Google faked brazenly Chromes user base until they made it, it was a coup d’état of the browser market.
@Rust Hurt
Not sure what you mean, independent data gathering repeatedly show Chromium at 80%+ market share. These numbers were / are not published by Google themselves at all.
uBlock eliminates 99% of these attacks.
chromium is the new adobe – avoid at all costs
Ya, you’re absolutely right. In the last months/versions, patch after patch almost every single week has been become the new normal for Chrome/Chromium and their offshoots.
it’s getting to the point where chromium is a free for all, look at all the zero days in the wild, and then look at the release notes for hundreds of severe critical patches each year
this is fast becoming a joke of adobe standards
https://docs.google.com/spreadsheets/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/edit#gid=2129022708
Oh boy, it’s negative IQ hour again in the gHacks comment section… When you have the overwhelming majority of the market, you are the most attractive target by far for hackers. If a vulnerability is actively exploited, you need to patch this quickly obviously.
That hackers don’t give as much of a f*ck about competing browsers due to their comparatively low market share (Firefox has 3% market share) doesn’t mean that your browser is materially more secure at all, because it really isn’t (see the article I’ve posted above), it just means that you are too irrelevant for adversaries to care at this point. I suppose you can sell your irrelevancy as a positive here, but implying that you are materially more secure than Chromium is factually wrong.
May I assume that you made the same assessments about Windows, ten or more ago when they too were the top of the heap and the focus of attack – still are?
If so, great job, if not, then please rethink the statements as hypocrisy because all that I heard and read was Windblows, oh, they have terrible security, patch Tuesday – you mean patch every day?
Windows did a poor job then and the ONLY reason they began throwing security money and personnel at their self-induced security issues were due to scrutiny and shame…
Anyone who goes along to get along in the security field is not a security professional. If the in-house coding is the issue, then it is on them. If the back-end being used is unchecked and used, it is on them…. on and on and on…. it’s on them, regardless of who they are – hard stop.
Market share has NOTHING to do with security and excuses for poor execution. Adobe, Java… nobody should get a pass of oops, sorry about running executable strings in our logs…WTH?
The browser it the endpoint and it requires more attention. Edge and so many others are Chromium based and that is what we have come to accept but it must be put into perspective and scrutinized like anything else.
All software vendors suffer vulns, and that is completely understandable, but constant issues is a lack of in-house Q&A, leadership, or one of many other issues – it is dysfunctional.
I wonder if Bromite is affected…
the more, the better (fixed!)
Speaking of Chrome, this browser will soon let you add notes to webpages (don’t confuse with the option to take a screenshot and making annotations on it). It’s something similar to the ‘comments’ you can add in Edge’s PDF reader:
https://redd.it/tmfyfg
.
Always mostly direct when I am reading about it I am updating any browser to the latest stable version.
This is because a browser is even with my ferry secure firewall, maybe even better antivirus program, and all the addons I have installed which are supposed to make the browser even more secure a ferry contamination admissible switch (link) from my computer.
Where is Edge patch ?
Patience my son, patience…
“Microsoft is aware of the recent Chromium security fixes. We are actively working on releasing a security patch.”
https://docs.microsoft.com/en-us/deployedge/microsoft-edge-relnotes-security#march-25-2022
Just released:
https://docs.microsoft.com/en-us/deployedge/microsoft-edge-relnotes-security
> Where is Edge patch ?
Security Update Guide – Microsoft
https://msrc.microsoft.com/update-guide
https://docs.microsoft.com/en-us/DeployEdge/microsoft-edge-relnotes-security
March 26, 2022
Microsoft has released the latest?Microsoft Edge Stable Channel (Version 99.0.1150.55), which incorporates the latest Security Updates of the Chromium project. This update contains a fix for CVE-2022-1096, which has been reported by the Chromium team as having an exploit in the wild. For more information, see the Security Update Guide
CVE-2022-1096 – Security Update Guide – Microsoft – Chromium: CVE-2022-1096 Type Confusion in V8
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-1096
Because of the urgency of the patch update for “zero-day attacks with confirmed exploits,” recommend that you apply the update manually (by downloading it) as soon as possible, instead of waiting for the roll-up automatic update, whose application timing is uncertain.
“Filthy hackers – how dare they exploit the vulnerabilities that we purposely built into the browser.”
Interesting theory andy..break the code and then give the illusion of “fixing it” in case of exploits..
Paranoia.?
I was really just making a comment on how Edward Snowden showed many years ago how Google was willing to build backdoors into its products for its financial partners in the various international spy agencies. So anytime a vulnerability is announced, you kind of have to ask the question if it was one of their “planned” vulnerabilities that hackers have located or one of their “oopsie” mistakes that hackers just happened to stumble across. Lots of highly paid and very smart people work at Google – they really shouldn’t have nearly as many problems as they do if they were all of the “oopsie” variety.
Brave released an “Upgraded Chromium to 99.0.4844.88” on March 26, 2012, with a patch (emergency update: Stable version 99.0.4844.84) for a vulnerability in the Chromium browser (zero-day attack that has been confirmed to be exploitable).
https://brave.com/latest/
Upgrade from Chromium 99.0.4844.83 to Chromium 99.0.4844.88. · Issue #21889 · brave/brave-browser · GitHub
https://github.com/brave/brave-browser/issues/21889
Of the major Chromium vendors,
Vivaldi and Opera have not released updated versions for this vulnerability (CVE-2022-1096) at this time, and not even a mention of it.
Vivaldi already updated: https://vivaldi.com/blog/desktop/minor-update-five-5-1/
@ShintoPlasm,
Thanks for the info.
At the time of my research (17:00 JST on 3/26), that information did not exist. I am glad you pointed out the latest situation and was able to correct the information to be accurate.
That’s why Brave is superior, they released a patch for this TEN YEARS AGO.
The mobile version of Chrome definitely hasn’t been released to the .84 version. It still shows as .73 in both Chrome and the Play Store, and this article is over 24 hours in age.
I got .88 this morning on Android 8
Please click on the following link to open the newsletter signup page: Ghacks Newsletter Sign up
Ghacks is a technology news blog that was founded in 2005 by Martin Brinkmann. It has since then become one of the most popular tech news sites on the Internet with five authors and regular contributions from freelance writers.
Author Profile
Latest entries
 राशीफल2024.04.23राशिफल : आज चमकेगा इन 5 राशियों का भाग्य, मनाएंगे जश्न – Hindustan
राशीफल2024.04.23राशिफल : आज चमकेगा इन 5 राशियों का भाग्य, मनाएंगे जश्न – Hindustan लाइफस्टाइल2024.04.23प्री-डायबिटीज का पता चलने पर अपने लाइफस्टाइल में करें इस तरह के बदलाव – TV9 Bharatvarsh
लाइफस्टाइल2024.04.23प्री-डायबिटीज का पता चलने पर अपने लाइफस्टाइल में करें इस तरह के बदलाव – TV9 Bharatvarsh विश्व2024.04.23हमास और इजरायल की जंग हुई खतरनाक, फिलिस्तीन को 22 अरब देशों का साथ; नेतन्याहू को दे डाली सलाह – Hindustan
विश्व2024.04.23हमास और इजरायल की जंग हुई खतरनाक, फिलिस्तीन को 22 अरब देशों का साथ; नेतन्याहू को दे डाली सलाह – Hindustan टेक2024.04.23NBN Australia Trials 100 Gbps FTTH Technology on Live Network – TelecomTalk
टेक2024.04.23NBN Australia Trials 100 Gbps FTTH Technology on Live Network – TelecomTalk